
When Cloudflare announced that their Tunnel service would become free, I saw an opportunity to strengthen the security of my private network. By using Cloudflare Tunnels together with Cloudflare WARP, you could close to your network router ports and access your entire private network in safer. Here’s how do it …
- The setup
- Step 1: Install “cloudflared” on your network
- Step 2: Setting up a Cloudflare Tunnel on the Raspberry Pi
- Step 3: Configure your Cloudflare Team
- Step 4: Configure your devices and Setup WARP application
- Step 5: configure split-tunnel
- All done!
- TIPS
- References
The setup
The idea of Cloudflare Tunnels is simple: connect your home network to Cloudflare’s network. Then use Cloudflare WARP to connect your devices to Cloudflare’s network and let it route traffic to your home.
Cloudflare WARP is an interesting service. It’s essentially a free VPN that protects your internet traffic by routing it through Cloudflare’s network. However, it has a killer feature: split-tunnels.
Normally, when you connect to a VPN server, all your internet traffic flows through that server. That means that your internet speed will depend on the connection speed of that server. Hosting a VPN server at home means your connection becomes as slow as your home’s upload speed, which is usually very slow. WARP will only send local traffic to your home. Your regular internet traffic stays blazing fast.
To follow along with this post, you’ll need:
- A Cloudflare and Cloudflare Teams account (both free)
- A small server or computer that’s always running on your home network
Step 1: Install “cloudflared” on your network
To install cloudflared, follow [Cloudflare’s documentation]. I installed it inside my Raspberry Pi server which required an additional dependency :
a. Our first task is to perform an update of the package list as well as upgrade any out-of-date packages.
1 | sudo apt update |
b. Once the update completes, we must ensure we have both the curl and lsb-release packages.
Install both of these packages by using the command below in the terminal.
1 | apt install curl lsb-release |
-
curl– We will use curl to grab the GPG key for the Cloudflared repository. -
lsb-release– This package allows us to easily retrieve information about the system, such as the release name.
c. With all the required packages in place, we can finally grab the GPG key for the cloudflared repository and store it on Raspberry Pi.
To save this key to your device, use the following command.
1 | curl -L https://pkg.cloudflare.com/cloudflare-main.gpg | sudo tee /usr/share/keyrings/cloudflare-archive-keyring.gpg >/dev/null |
A GPG key is crucial to verify the packages we are installing are valid and belong to the repository.
d. With the GPG key saved into our keyrings folder, our next step is to add the Cloudflared repository to our Raspberry Pi. You can add
1 | echo "deb [signed-by=/usr/share/keyrings/cloudflare-archive-keyring.gpg] https://pkg.cloudflare.com/cloudflared $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/cloudflared.list |
e. As we have made changes to the available repositories, we will need to perform another update of the package list cache,
You can update this cache by using the following command within the terminal.
1 | apt update |
f. With the repository added, we can now proceed to install the Cloudflared package to our Raspberry Pi. To connect a private network to Cloudflare, a daemon must run on a computer inside that network. Here, that’s cloudflared and it will open a tunnel from within your network, so no ports have to be opened.
1 | apt install cloudflared |
1 | Reading package lists... Done |
g. You can install cloudflared as a system service on Linux and Windows, and as a launch agent on macOS (here more information). In most cases, I recommend running cloudflared as a service. Running as a service helps ensure the availability of cloudflared to your origin by allowing the program to start at boot and continue running while your origin is online.
1 | cloudflared service install |
1 | 2022-12-22T06:04:36Z INF Using Systemd |
1 | systemctl start cloudflared.service |
1 | systemctl status cloudflared.service |
1 | ● cloudflared.service - cloudflared |
Step 2: Setting up a Cloudflare Tunnel on the Raspberry Pi
Now that we have prepared our Raspberry Pi, we can set up the Cloudflare tunnel. This tunnel is where your traffic will be run over
a. Our first step is to create an association between our Raspberry Pi and the Cloudflare service.
We can begin authenticating with the Cloudflare service by using the command below.
1 | cloudflared tunnel login |
Ensure you keep Cloudflared open on your device while this process is completed.
You will want to go to the URL displayed in the message and use it to log in to your Cloudflare account.
1 | Please open the following URL and log in with your Cloudflare account: |
Because we run cloudflared in console, we need to copy provided URL, and paste it into web browser, after log in, we need to choose domain we own to use.
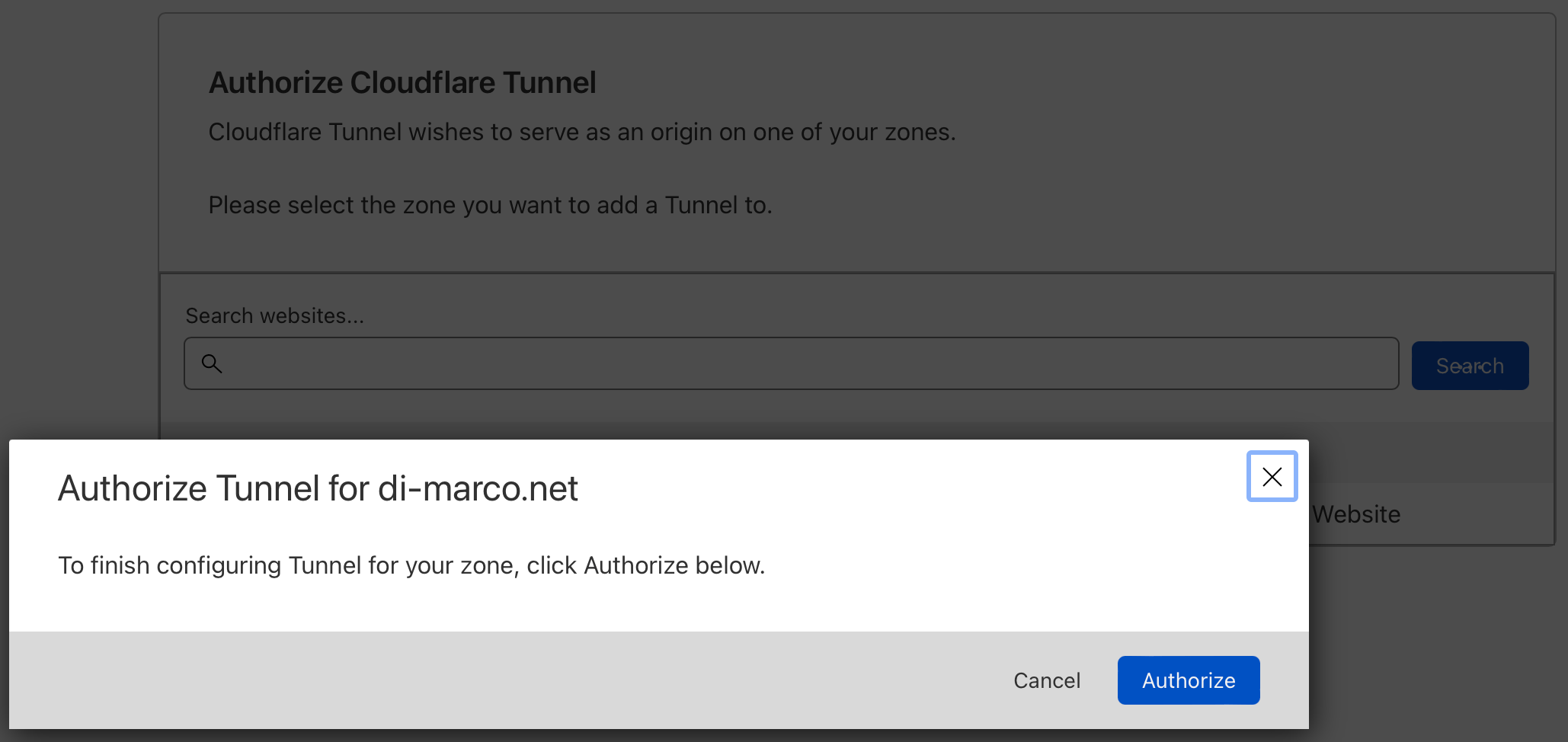
Once your Raspberry Pi is successfully authenticated with the Cloudflare service, you will see the following message.
1 | 2022-12-20T10:42:05Z INF Waiting for login... |
We see on the terminal, that cloudflared downloaded certificate (in /root/.cloudflared/cert.pem) which will be used for authenticate tunnel connection to the Cloudflare data center.
c. Now, is time to create our tunnel, create it just by typing cloudflare tunnel create <tunel-name>, you will get unique tunnel ID in return, which will be needed later on:
1 | cloudflared tunnel create n0d3-VPC-r5d4 |
1 | Tunnel credentials written to /root/.cloudflared/6dxxxx1a-xxxx-4xx4-axx1-c37xxxxa04f1.json. `cloudflared` chose this file based on where your origin certificate was found. Keep this file secret. To revoke these credentials, delete the tunnel. |
1 | cat /root/.cloudflared/6dxxxx1a-xxxx-4xx4-axx1-c37xxxxa04f1.json |
1 | {"AccountTag":"xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx","TunnelSecret":"xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx=","TunnelID":"6dxxxx1a-xxxx-4xx4-axx1-c37xxxxa04f1"} |
If there is need to list created tunnels and its ID, just type in cloudflared tunnel list
1 | cloudflared tunnel list |
1 | You can obtain more detailed information for each tunnel with `cloudflared tunnel info <name/uuid>` |
1 | cloudflared tunnel info 6d99241a-9e35-4034-ab51-c372504a04f1 |
1 | NAME: n0d3-VPC-r5d4 |
d. We reach to the most important part in this section. To be able route packet through tunnel for private network ranges we need:
- First, create Cloudflare Gateway and modify policies - which we have done already
- Second, add routing for our home, private network range, which we will do it now
Replace network range with you own.
Example below, tels Cloudflare that if you see packet from 192.168.xx.0/24 network, route them through tunnel ID 6dxxxx1a-xxxx-4xx4-axx1-c37xxxxa04f1.
1 | cloudflared tunnel route ip add 192.168.xx.0/24 6dxxxx1a-xxxx-4xx4-axx1-c37xxxxa04f1 |
1 | Successfully added route for 192.168.xx.0/24 over tunnel 6dxxxx1a-xxxx-4xx4-axx1-c37xxxxa04f1 |
To check, which routes was defined, just type cloudflared tunnel route ip show
1 | cloudflared tunnel route ip show |
1 | NETWORK VIRTUAL NET ID COMMENT TUNNEL ID TUNNEL NAME CREATED DELETED |
e. Last step, which need to be done on the Raspberry Pi is create config file, where we gather all needed configuration to run the cloudflared tunnel.
To establish tunnel, we need to pass tunnel ID, which cloudflared should run and credentials to it - we got it before, while creating tunnel above.
1 | cat /root/.cloudflared/config.yml |
1 | tunnel: 6dxxxx1a-xxxx-4xx4-axx1-c37xxxxa04f1 |
Time to run it!
1 | cloudflared tunnel run |
1 | 2022-12-20T11:31:22Z INF Starting tunnel tunnelID=6dxxxx1a-xxxx-4xx4-axx1-c37xxxxa04f1 |
or with
1 | systemctl start cloudflared.service |
And check with :
1 | systemctl status cloudflared.service |
1 | ● cloudflared.service - cloudflared |
As of quic-go v0.19.x, you might see warnings about the receive buffer size.
It is recommended to increase the maximum buffer size by running:sudo sysctl -w net.core.rmem_max=2500000
This command would increase the maximum receive buffer size to roughly 2.5 MB.
Step 3: Configure your Cloudflare Team
Next, you need to make sure that not everyone can login to your Cloudflare Team. You’ll need to add some restrictions.
Here you can create a rule that only allows people with a certain email address to access your Cloudflare Team and the tunnels assigned to it. I whitelisted everyone with an @di-marco.net address:
Head over the Cloudflare Teams Dashboard > Settings > WARP Client > Device enrollment and click on “Manage”:
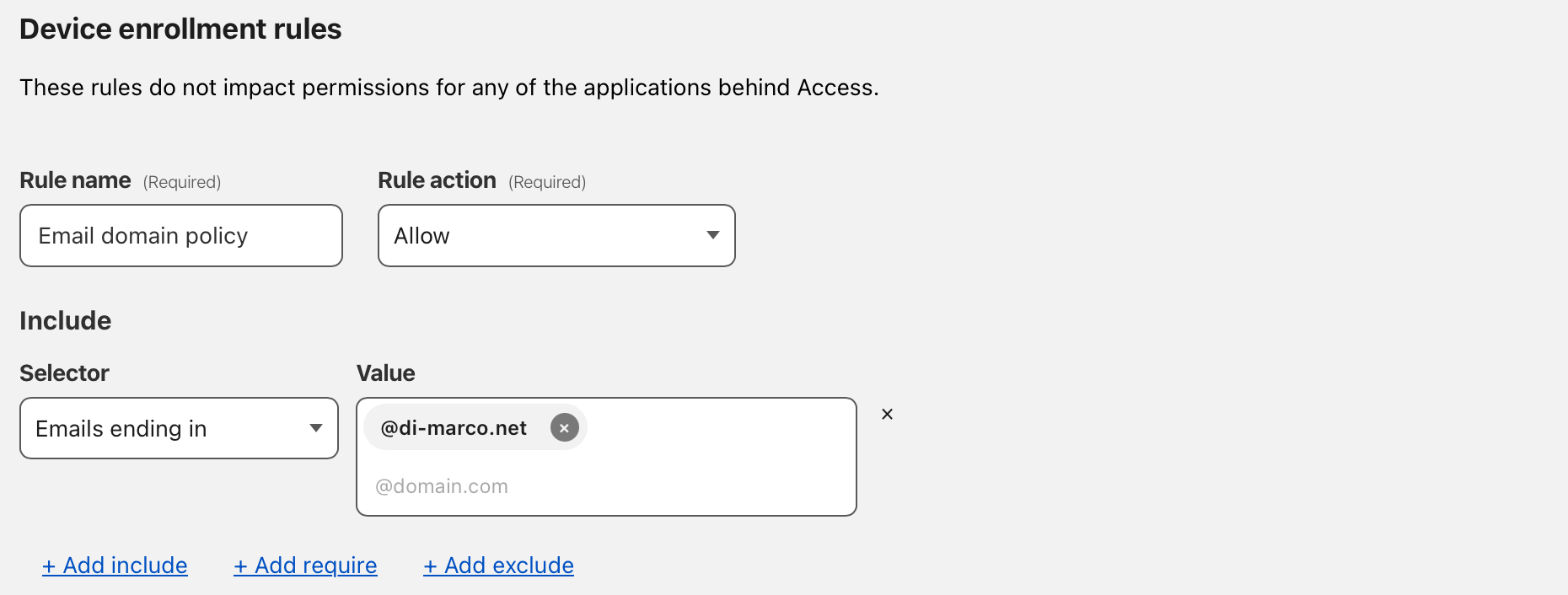
Step 4: Configure your devices and Setup WARP application
Now we need to install WARP application (download it) on our devices, which enable them to connect/ route traffic to your private network.
Start by installing Cloudflare WARP on your devices. The app acts as a free VPN service and protects your internet traffic on untrusted networks. However, we want to use it to access our tunnel.
To do that, open WARP’s preferences, go to “Account” and click “Login with Cloudflare for Teams”.
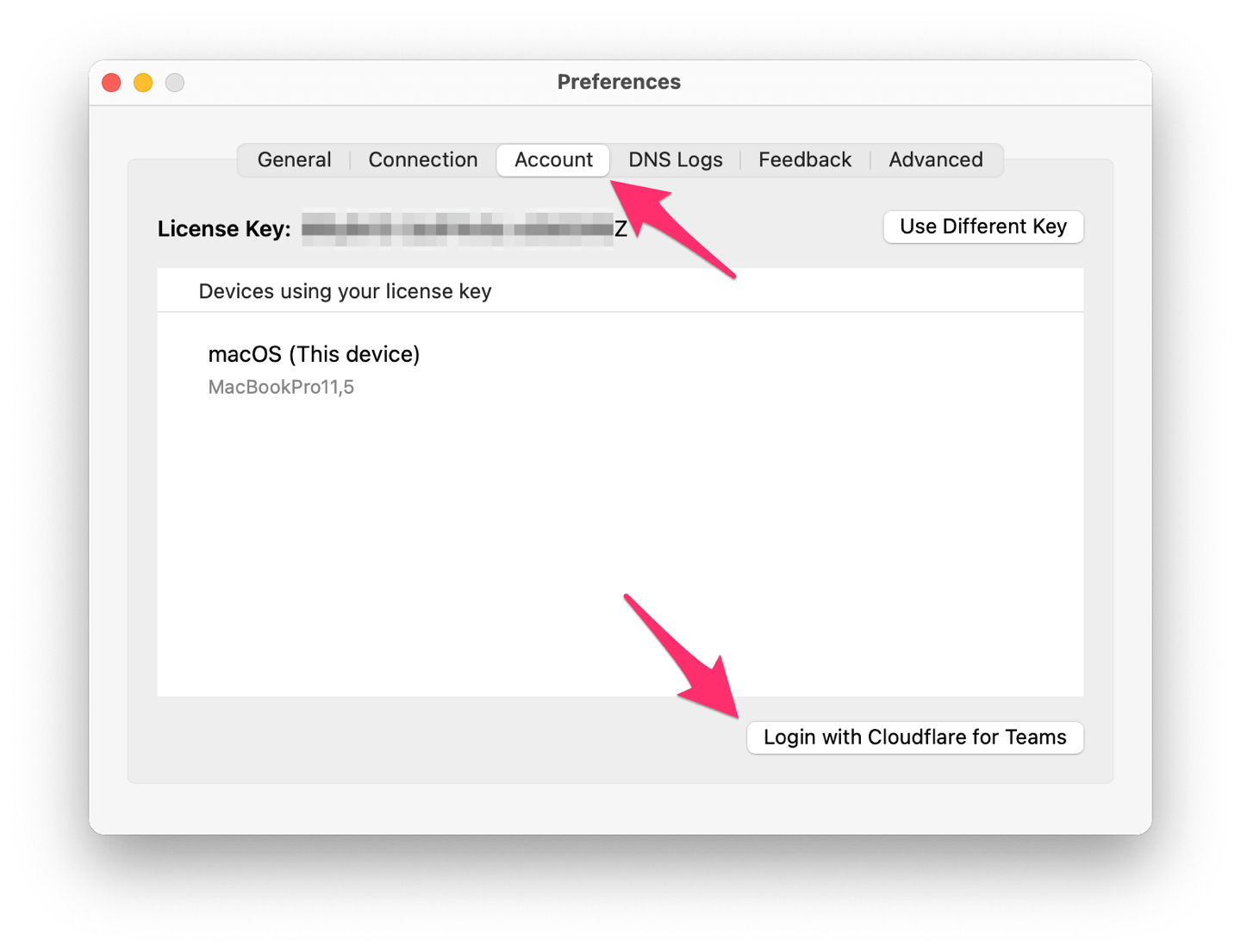
Login with your Cloudflare Teams account and afterwards, the WARP client will show that you’re part of a team:
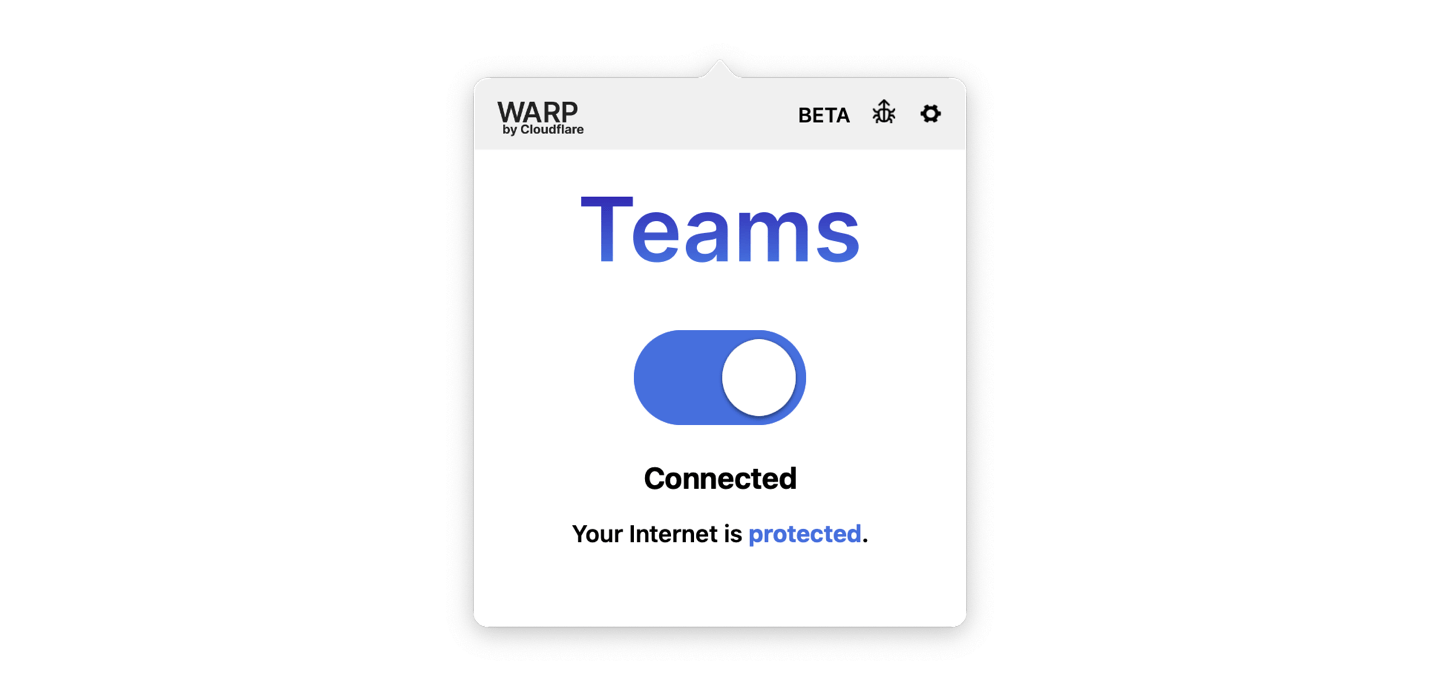
Step 5: configure split-tunnel
Last step is to configure WARP’s “split-tunnel” feature. By default, WARP will exclude traffic to local IP addresses, meaning it will not route these requests to your private network.
To manage this, go to Cloudflare Teams Dashboard > Settings > WARP Client > Device settings > Configure settings > Split tunnels. Make sure that your home network is not in the list. For me, that meant removing the good entry (for example 192.168.0.0/16 if it range of your home network).
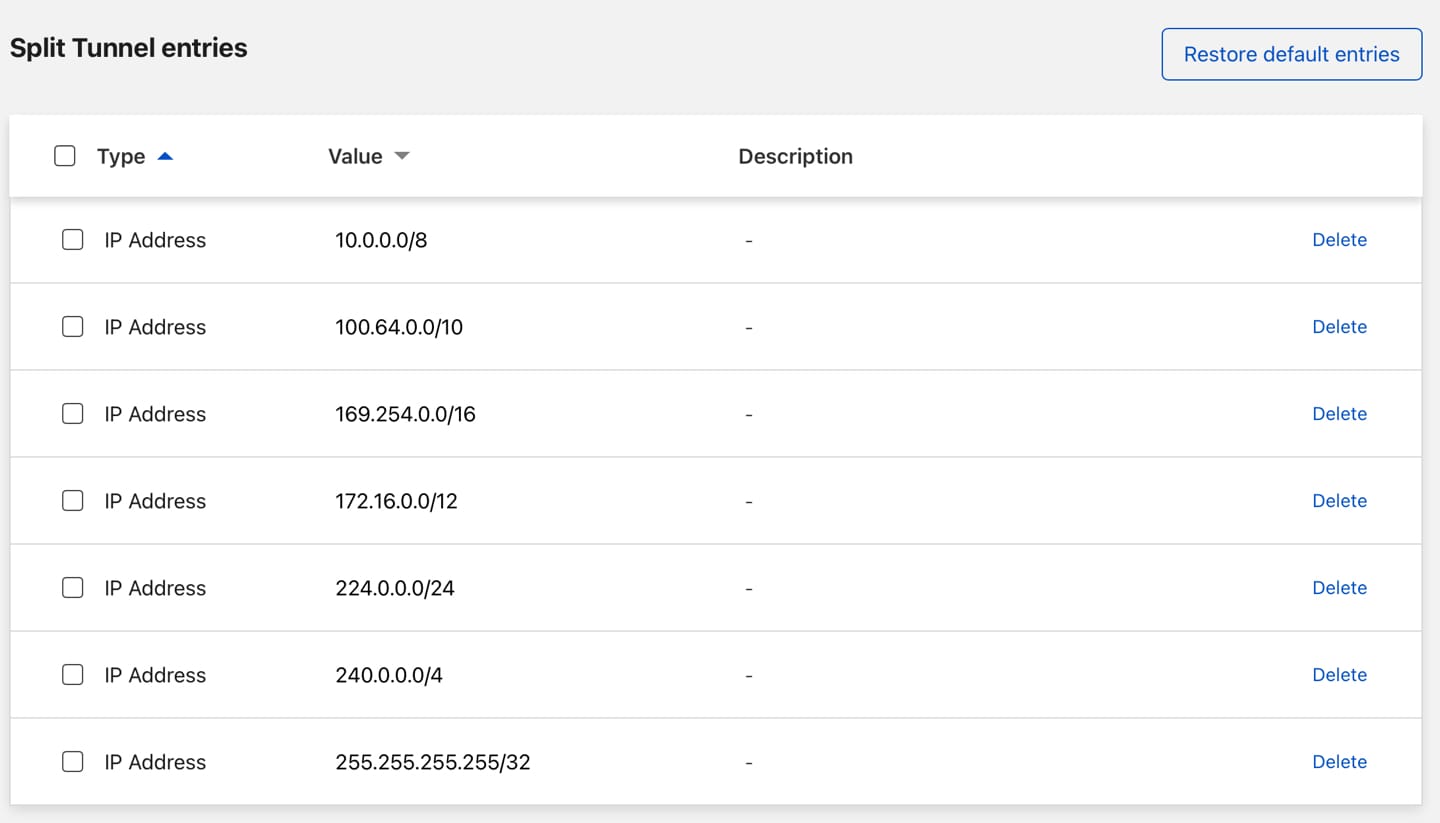
Make sure that your home network range isn’t listed here. Otherwise it won’t be routed over the tunnel.
That’s it! Go back to the WARP client on your device and let it connect to Cloudflare. Once connected, you should be able to access your home network and all services running inside it. Regardless of where you are!
All done!
So now you have…
- A free VPN-service to protect your internet traffic on untrusted networks (which automatically turns on and off)
- A way to (securely) access your entire home network without opening ports
Some people might disagree with the “secure” part and say that Cloudflare shouldn’t be trusted.
TIPS
Tips : Automatically connect to WARP
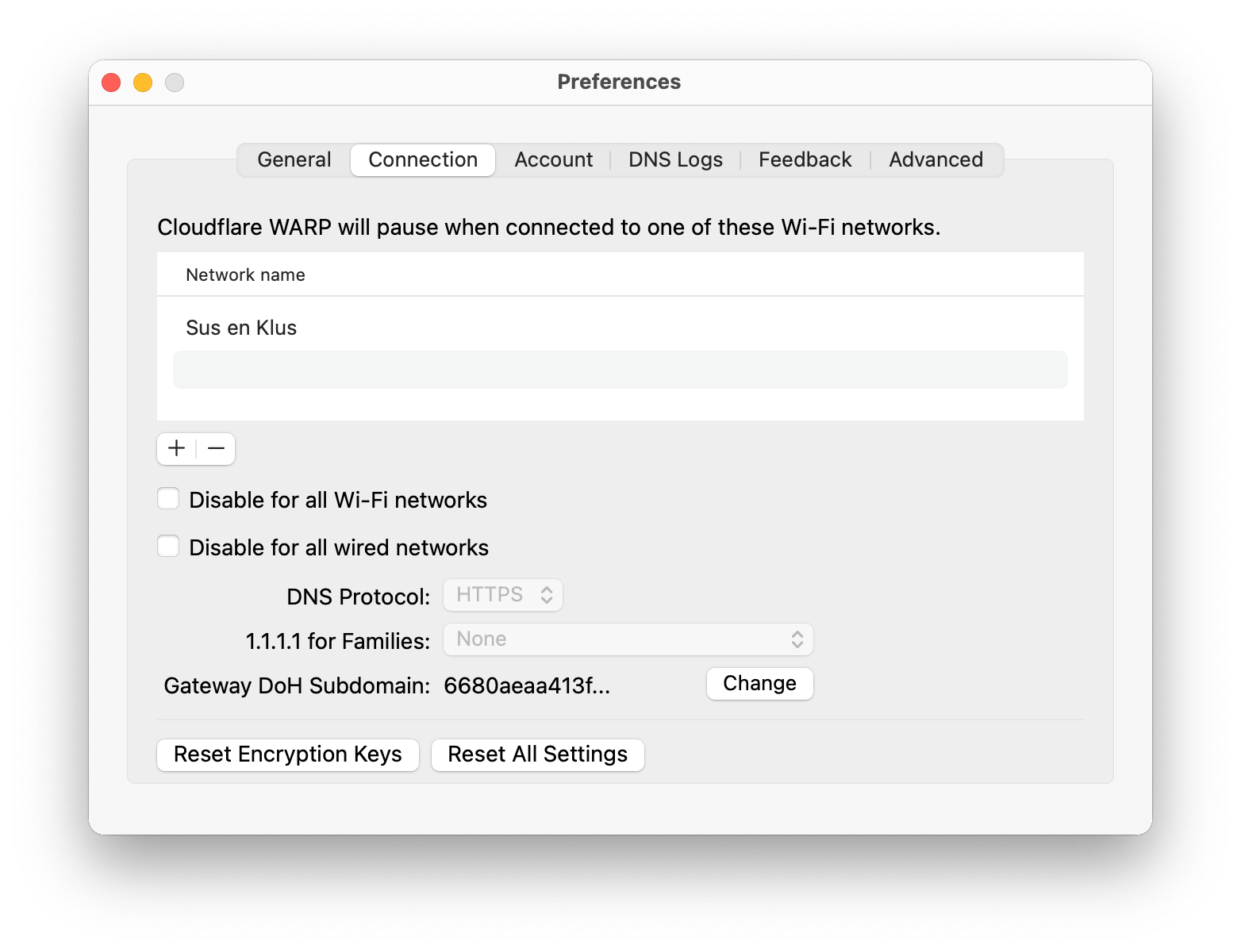
You can even configure WARP to activate itself when you’re connected to an unknown Wi-Fi network.
In the preferences, you can list your trusted Wi-Fi networks. When you’re connected to these, WARP will deactivate itself. Connect to a Wi-Fi hotspot and WARP will automatically protect your traffic and give you access to your home network.
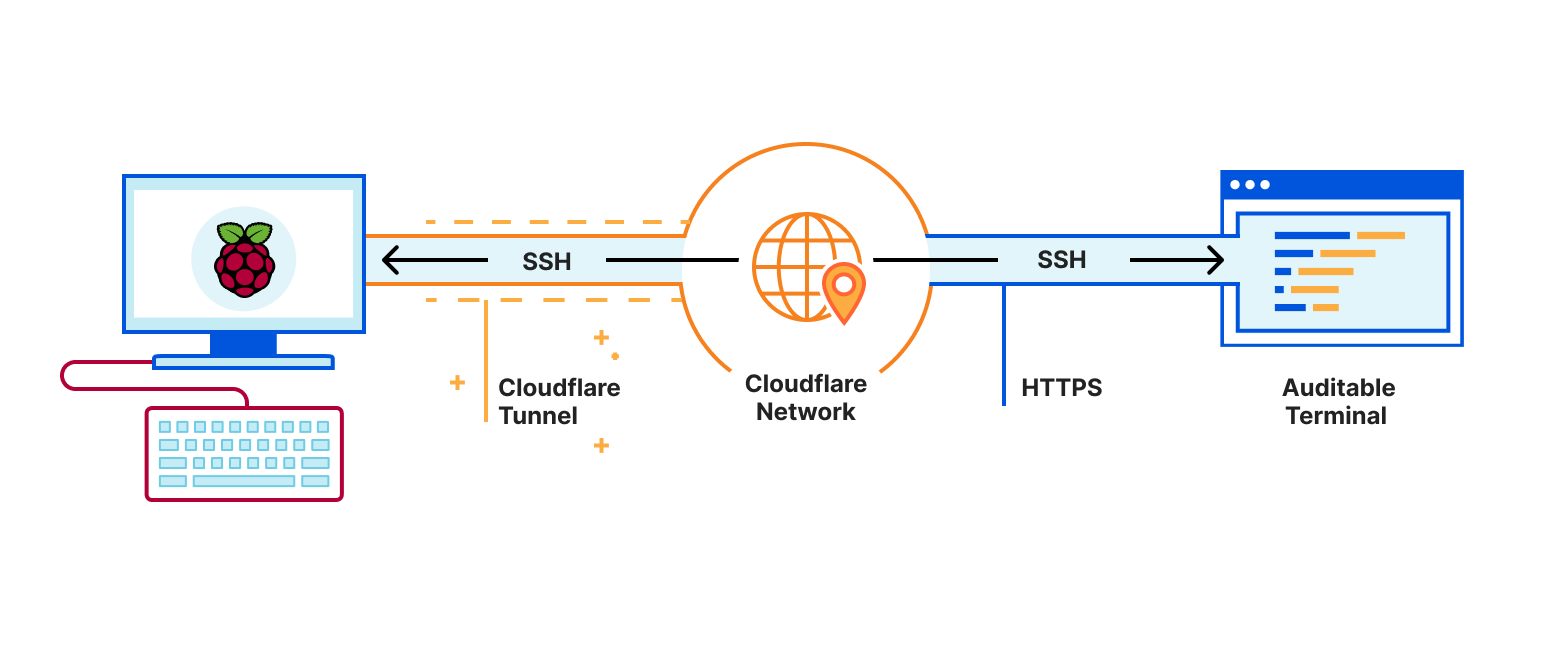
Tips : SSHing from a browser, with Cloudflare Tunnel and Auditable Terminal
Auditable Terminal gives you a fully featured SSH client in your browser. You authenticate using Cloudflare Access and can log into a computer from anywhere just using the browser and get a terminal. And using Cloudflare Tunnel you can securely connect a computer to Cloudflare without punching holes in a firewall. And you end up with a consistent terminal experience across devices: 256 colours, Unicode support and the same fonts everywhere.
To expose a local web service, edit your config.yml file and add an ingress section:
1 | cat /root/.cloudflared/config.yml |
1 | tunnel: 6dxxxx1a-xxxx-4xx4-axx1-c37xxxxa04f1 |
And finall, you just needed to tell cloudflared to route sshing.mydomain.com to the tunnel.
1 | CNAME `sshing.mydomain.com` -> YOUR-TUNNEL-UUID-HERE.cfargotunnel.com |
with command below
1 | cloudflared tunnel route dns 6dxxxx1a-xxxx-4xx4-axx1-c37xxxxa04f1 sshing.mydomain.com |


